The Security Risk Assessment Checklist Template You Need Right Now
In today’s interconnected world, data breaches, cyberattacks, and system failures are constant threats. Protecting your valuable information and assets requires a proactive approach, and that’s where a robust security risk assessment comes in. But where do you begin? This article dives deep into the importance of a security risk assessment and provides a comprehensive checklist template to help you identify vulnerabilities, assess risks, and implement effective security controls. Forget the guesswork; this is your guide to building a stronger security posture.
Why a Security Risk Assessment is Non-Negotiable
A security risk assessment isn’t just a good idea; it’s a fundamental requirement for any organization serious about protecting its data and reputation. Ignoring this crucial step leaves you vulnerable to:
- Financial Loss: Costs associated with data breaches can include remediation, legal fees, regulatory fines, and lost business.
- Reputational Damage: A security incident can severely damage customer trust and brand image.
- Operational Disruptions: Cyberattacks can cripple your operations, leading to downtime and lost productivity.
- Legal and Regulatory Non-Compliance: Many industries have specific security requirements, and failing to meet them can result in hefty penalties.
A well-executed risk assessment allows you to proactively identify potential threats, understand their impact, and implement appropriate safeguards to mitigate them. It’s the foundation upon which you build a resilient and secure organization.
Your Essential Security Risk Assessment Checklist Template
This checklist provides a structured framework for assessing your organization’s security posture. Remember to tailor this template to your specific needs and industry.
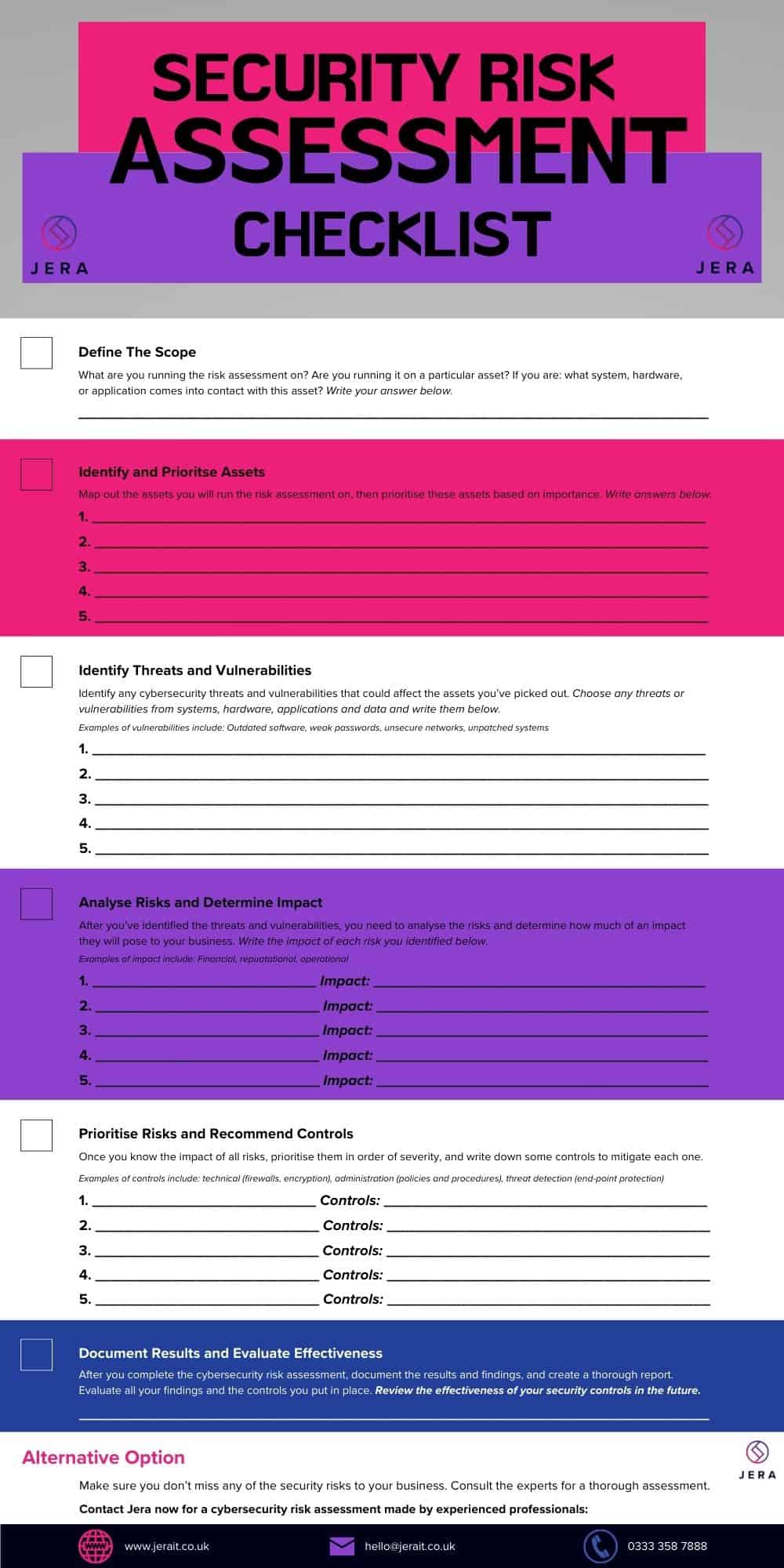
I. Scope and Context Definition:
- Define Scope: Clearly outline the systems, networks, data, and assets that will be included in the assessment.
- Identify Stakeholders: Determine who will participate in the assessment, including IT staff, department heads, and security professionals.
- Define Objectives: Establish the goals of the assessment (e.g., identify vulnerabilities, comply with regulations, improve security posture).
- Gather Information: Collect relevant documentation, such as network diagrams, security policies, and incident reports.
- Legal and Regulatory Requirements: Identify any relevant laws, standards, or regulations that apply to your organization (e.g., GDPR, HIPAA, PCI DSS).
II. Asset Identification and Valuation:
- Identify Critical Assets: Determine the most important assets (data, systems, applications, infrastructure) that need protection.
- Categorize Assets: Group assets based on type, function, and sensitivity.
- Determine Asset Value: Assign a value to each asset based on its importance to the business, considering factors like cost of replacement, revenue impact, and legal implications.
- Document Asset Details: Create a comprehensive inventory of all assets, including their location, owner, and current security controls.
III. Threat Identification:
- Identify Potential Threats: Brainstorm a list of potential threats that could exploit vulnerabilities in your assets. Consider:
- External Threats: Malware, phishing attacks, social engineering, denial-of-service (DoS) attacks, insider threats (malicious and unintentional).
- Internal Threats: Employee negligence, disgruntled employees, accidental data loss.
- Environmental Threats: Natural disasters, power outages, physical security breaches.
- Threat Modeling: Use threat modeling techniques (e.g., STRIDE, PASTA) to analyze potential attack vectors.
- Consider Threat Actors: Identify the likely threat actors (e.g., cybercriminals, nation-states, competitors) and their motivations.
IV. Vulnerability Analysis:
- Identify Vulnerabilities: Determine weaknesses in your systems, networks, and processes that could be exploited by threats. Consider:
- Technical Vulnerabilities: Software bugs, configuration errors, unpatched systems, weak passwords.
- Physical Vulnerabilities: Lack of physical security controls, inadequate access controls.
- Procedural Vulnerabilities: Inadequate security policies, lack of employee training, poor incident response procedures.
- Vulnerability Scanning: Utilize vulnerability scanning tools to identify known vulnerabilities in your systems.
- Penetration Testing: Conduct penetration testing to simulate real-world attacks and identify exploitable vulnerabilities.
- Review Security Configurations: Audit system configurations to ensure they align with security best practices.
V. Risk Analysis and Evaluation:
- Assess Likelihood: Determine the probability of each threat exploiting a vulnerability. Consider historical data, threat intelligence, and industry trends.
- Assess Impact: Evaluate the potential impact of each threat exploiting a vulnerability, considering factors like financial loss, reputational damage, operational disruption, and legal repercussions.
- Calculate Risk Level: Use a risk matrix or other scoring system to calculate the overall risk level for each threat-vulnerability pairing. Risk is typically calculated as the product of likelihood and impact.
- Prioritize Risks: Rank risks based on their severity, allowing you to focus on the most critical threats first.
VI. Control Implementation and Mitigation:
- Identify Existing Controls: Document all current security controls in place (e.g., firewalls, intrusion detection systems, access controls, data encryption).
- Evaluate Control Effectiveness: Assess the effectiveness of existing controls in mitigating identified risks.
- Develop Mitigation Strategies: Develop plans to address identified risks, including:
- Risk Avoidance: Eliminate the risk by discontinuing the activity or changing the process.
- Risk Transfer: Transfer the risk to a third party (e.g., insurance).
- Risk Mitigation: Implement security controls to reduce the likelihood or impact of the risk.
- Risk Acceptance: Accept the risk if the cost of mitigation outweighs the potential impact.
- Implement Security Controls: Implement the chosen mitigation strategies, including:
- Technical Controls: Firewalls, intrusion detection/prevention systems (IDS/IPS), antivirus software, data encryption, multi-factor authentication (MFA).
- Administrative Controls: Security policies, procedures, training, awareness programs, incident response plans.
- Physical Controls: Access controls, surveillance systems, security guards.
- Document Control Implementation: Record all implemented controls, their purpose, and their configuration.
VII. Reporting and Documentation:
- Create a Risk Assessment Report: Document the entire assessment process, including:
- Scope and objectives
- Assets identified
- Threats and vulnerabilities identified
- Risk analysis and evaluation
- Mitigation strategies
- Implemented controls
- Communicate Findings: Share the report with relevant stakeholders, including management, IT staff, and security teams.
- Develop a Remediation Plan: Create a plan for addressing identified vulnerabilities and implementing recommended controls.
- Update Documentation: Keep all security documentation up-to-date, including policies, procedures, and network diagrams.
VIII. Monitoring and Review:
- Implement Security Monitoring: Monitor systems and networks for security events and incidents.
- Conduct Regular Reviews: Review the risk assessment regularly (e.g., annually, or more frequently if there are significant changes to the environment).
- Update the Risk Assessment: Revise the risk assessment based on changes in the environment, new threats, and the effectiveness of implemented controls.
- Continuous Improvement: Continuously improve your security posture based on the results of monitoring and reviews.
Conclusion: Securing Your Future with Proactive Security
Implementing a security risk assessment is not a one-time task, but an ongoing process. By using this checklist template, you can take a proactive approach to identifying, assessing, and mitigating security risks, ultimately building a stronger and more resilient organization. Remember to regularly review and update your assessment to stay ahead of evolving threats and ensure the continued protection of your valuable assets. Don’t wait for a breach; start securing your future today.
Frequently Asked Questions (FAQs)
1. How often should I conduct a security risk assessment?
The frequency of your risk assessment depends on various factors, including the size and complexity of your organization, the sensitivity of your data, and the regulatory landscape. However, a minimum of once a year is generally recommended. More frequent assessments may be necessary if there are significant changes to your environment (e.g., new systems, applications, or infrastructure) or if there’s a major security incident.
2. What tools can I use for a security risk assessment?
A variety of tools can assist with the assessment process. These include vulnerability scanners (e.g., Nessus, OpenVAS), penetration testing tools (e.g., Metasploit, Burp Suite), risk assessment software (e.g., LogicManager, Reciprocity), and various security information and event management (SIEM) solutions.
3. Who should be involved in the security risk assessment process?
A successful risk assessment requires input from a diverse group of stakeholders. This should include IT staff, security professionals, department heads, and potentially legal and compliance personnel. The involvement of employees from different departments ensures a comprehensive understanding of the organization’s assets, threats, and vulnerabilities.
4. What is the difference between a vulnerability assessment and a risk assessment?
A vulnerability assessment focuses solely on identifying vulnerabilities in your systems and networks. A risk assessment, on the other hand, goes further by analyzing the potential impact of those vulnerabilities being exploited. Risk assessments incorporate the likelihood of a threat exploiting a vulnerability, the potential impact, and the existing controls in place to mitigate the risk.
5. Is this checklist a substitute for a security professional?
While this checklist provides a valuable framework, it is not a substitute for the expertise of a qualified security professional. Consider consulting with a security expert, especially if you lack the internal resources or expertise to conduct a thorough assessment. A professional can help you tailor the checklist to your specific needs, identify hidden vulnerabilities, and develop effective mitigation strategies.